Introduction
After analyzing my Postfix server’s activity graph using Zabbix, I discovered that every 5 minutes, an attacker attempts brute-force login attempts. To prevent this, I decided to manually configure firewall rules and demonstrate how to create an IP blacklist rule.
On my Ubiquiti UniFi UXG-Lite router, it is possible to block specific IP addresses or subnets by creating Network Objects and using Firewall Policy.
Creating a Blacklist Group
A blacklist is a list of IP addresses and/or subnets, organized as a network object group. To create such a group, follow these steps:
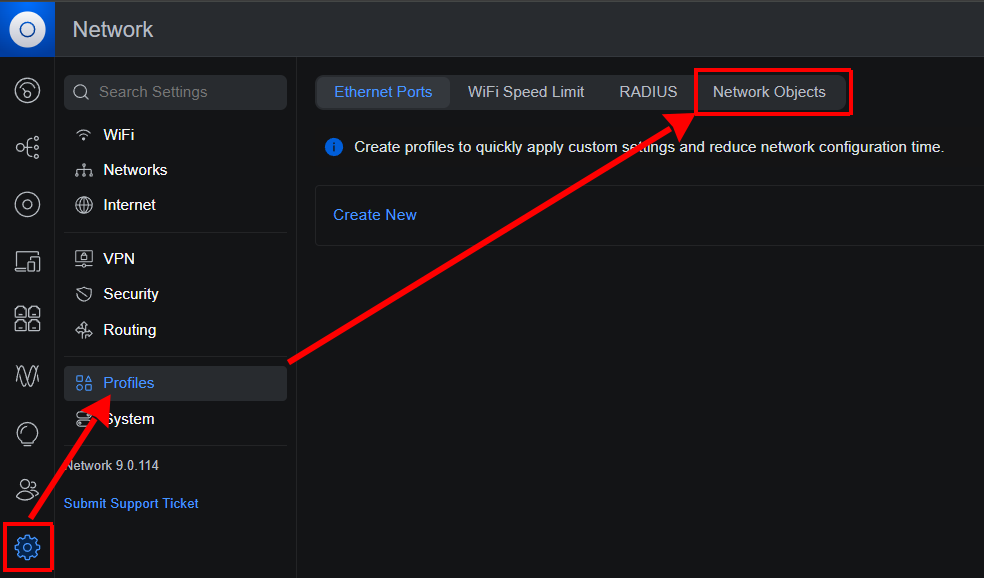
- Click the Settings (gear icon) menu.
- Select Profiles.
- Navigate to Network Objects.
- Click Create New.
In the Network Objects screen, fill in the following fields:
- Object Name – e.g., Postfix Black List.
- Type – Select “IPv4 Address/Subnet” from the dropdown list.
- Address – Enter the first IP address or subnet.
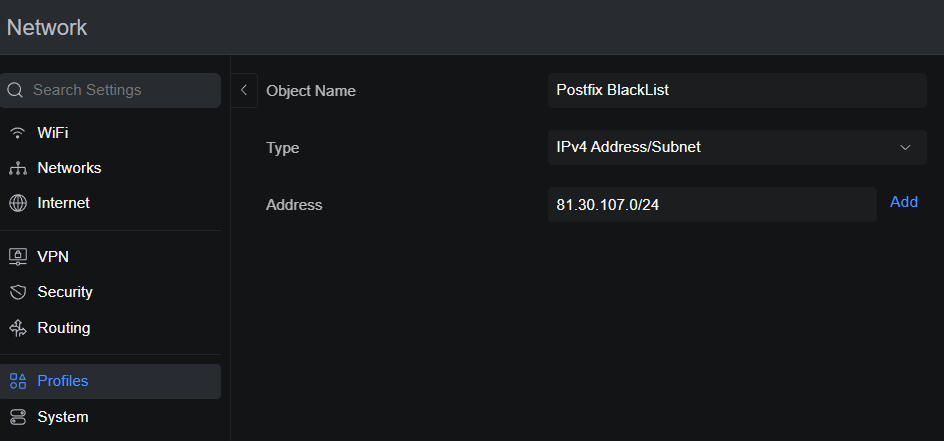
Click Add to create the list and apply the changes.
Creating a Blocking Rule for Ubiquiti UniFi Zone-Based Firewall
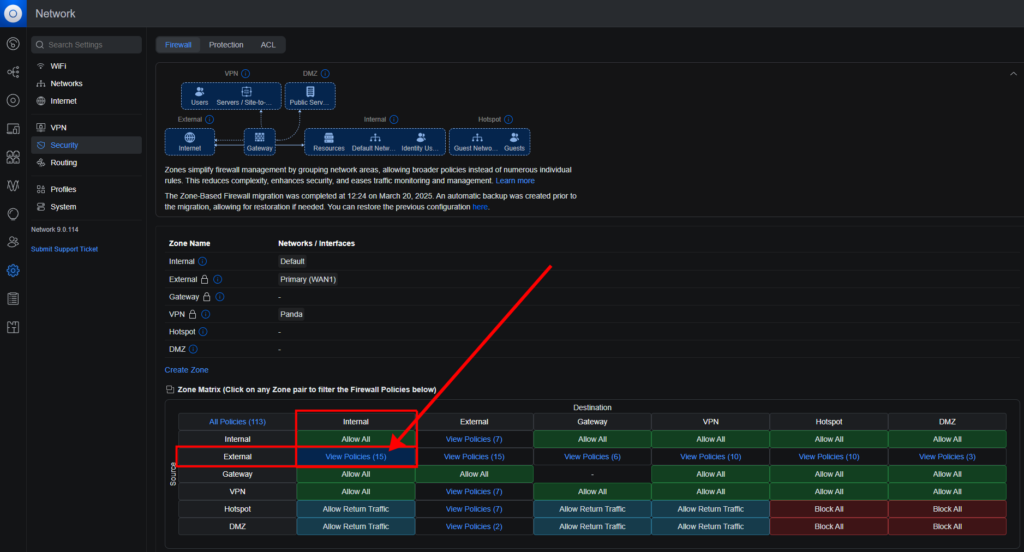
Given that my router has been updated, a new feature has been activated – Zone-Based Firewall. It visually divides rules into groups according to their type. Therefore, I will make settings in the new interface, where rules are already called policies.
According to the zone table, the policy must be added to the cell at the intersection of Source External and Destination Internal. To do this, click on the cell and at the very bottom of the policy list, click on the Create Policy button.
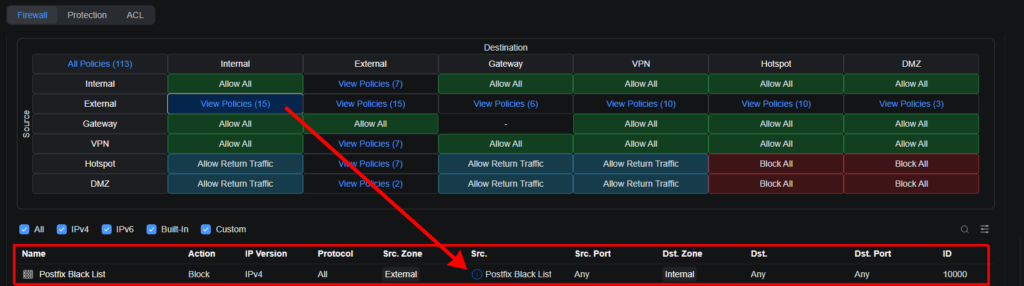
The principle of the policy is simple:
- Detect external traffic for the presence of IP addresses and/or subnets that are blacklisted
- Block traffic from the corresponding IP addresses and/or subnets, provided that the traffic is directed to the local network.
This setting appeared only in Zone-Based Firewall, because before this innovation it was possible to block all traffic. Now the settings are more flexible, so such a policy can be created for each zone separately.
A sidebar will open on the right, where you need to fill in the appropriate fields. The fields are grouped by blocks to make it easier to navigate the settings:
Name: Postfix Black List.
Source Zone block
- The External value will be the default if the required cell in the Zone-Based Firewall table was previously specified, otherwise you must select the External value
- Select the IP value
- Select the Object value
- From the drop-down list, select the previously created Postfix Black List group
- Select the value Port: Any
Action block
- Select the Block value
Destination Zone block
- The Internal value will be the default if the required cell in the Zone-Based Firewall table was previously specified, otherwise you must select the Internal value
- Select the Any value
- Select the value Port: Any
Additional settings block
- IP Version: IPv4
- Protocol: All
- Connection State: All
- Syslog Logging: checkbox enabled
- Schedule: Always
- Description: Block all IP’s from the Postfix blacklist
Click Add Policy. The new rule will appear in the list and be applied immediately.
Verifying Policy Functionality
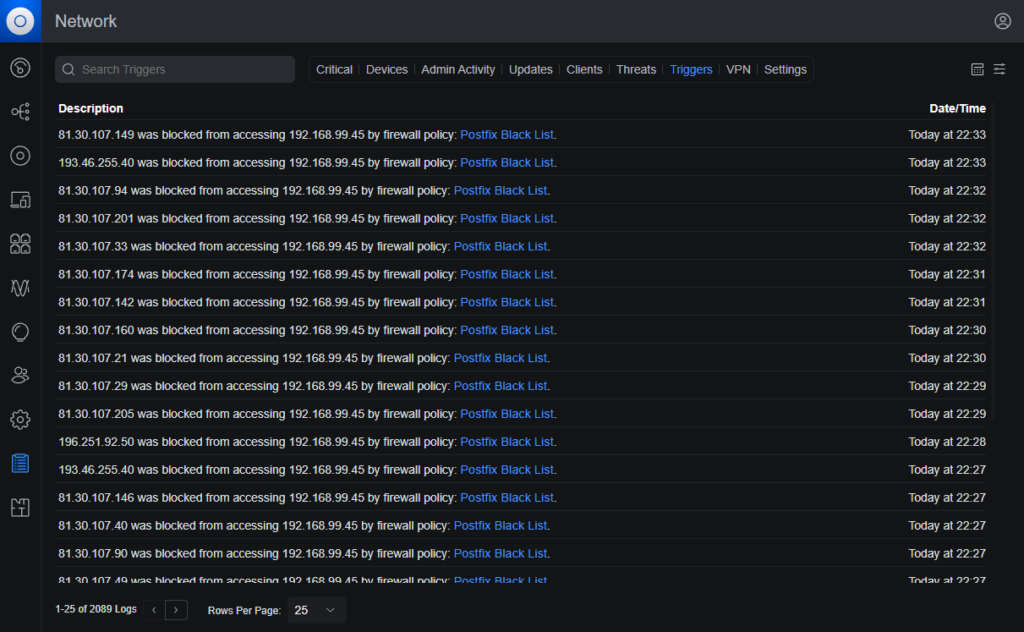
Blocked traffic logs can be found in the System Log under the Triggers tab. You can review individual entries to confirm that the policy is working as expected.
Conclusion
The Zone-Based Firewall feature in Ubiquiti UniFi allows effective blocking of unwanted traffic using IP blacklists. Utilizing Network Objects and flexible policies in the new interface simplifies network security management.





